Configure AGW for End-to-End SSL/TLS Encryption with Cloudflare (AKS Part 3)
This is the third installment of my Azure Kubernetes Service series. In this part, we will configure end-to-end SSL/TLS encryption for Azure Application Gateway (AGW) using Cloudflare. Initially, Cloudflare is set up to handle DNS, caching, and security enhancements. The next steps involve creating an origin certificate directly from Cloudflare and uploading this certificate to AGW. Additionally, we can store the certificate in Azure Key Vault (AKV), and have the AGIC ingress automatically pull and upload the certificate to AGW. Finally, AGW is configured to utilize this certificate, ensuring SSL/TLS encryption across all transmitted data and securing communication from the origin to the end user. You can check out the first two parts of the series here: Part 1 Part 2
Secure our Application with SSL/TLS end-to-end encryption
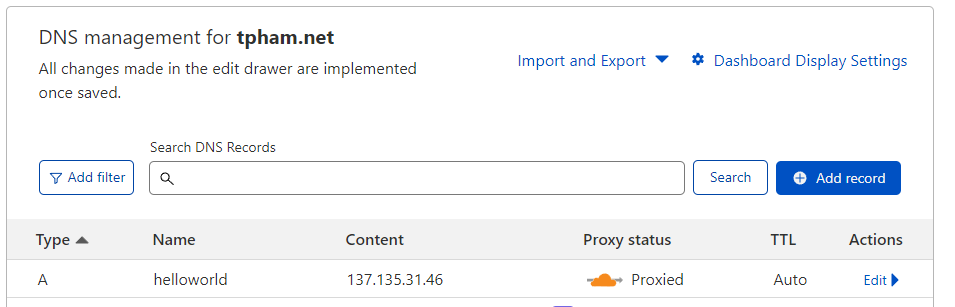
We going to use CloudFlare to setup a custom domain for our application. We need to create proxied A or CNAME records. The user connection will go to Cloudflare, Cloudflare will do its thing and then connect to the public IP of our AGW, returning the results to the user.
We can check our AGW public IP in the Azure portal or from the AGIC ingress we setup earlier.
kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
hello-world-ingress <none> * 137.135.31.46 80 24m
Add a DNS record that point our domain to the AGW public IP address. Make sure proxying is turned on (orange cloud).
We now need to generate an origin certificate we can install on AGW and secure our site with end-to-end encryption.
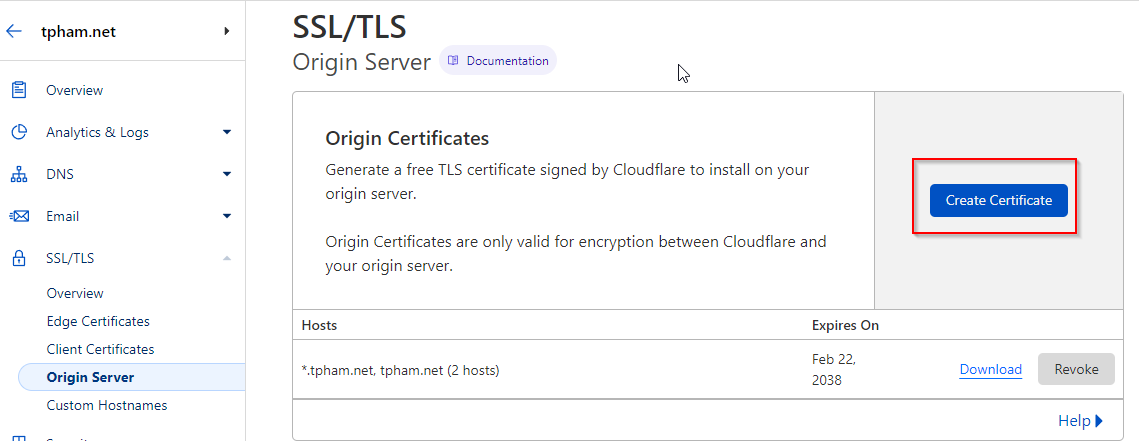
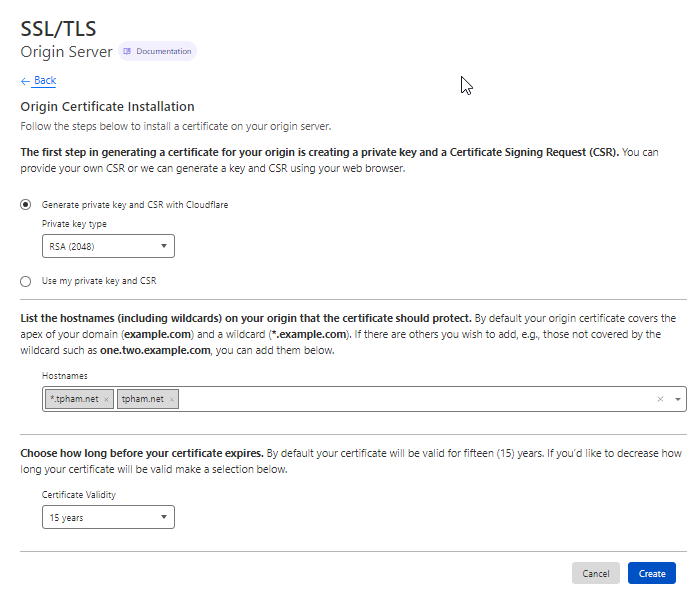
After you create, you will get your certificate and private key in PEM format (default), which you can use to create the .pfx file. Copy and paste the certificate and private key to separate text files, for example tpham.pem and tpham.key. You can now use openssl to generate the .pfx file, make sure to give your certificate a password.
Example:
openssl.exe pkcs12 -export -out tpham-cert.pfx -inkey tpham.key -in tpham.pem
Now that we have our certificate .pfx file. We can manually upload the certificate into our AGW or we can store it in AKV and have AGIC ingress pull automatically upload the certificate to AGW.
az network application-gateway ssl-cert create -g myResourceGroup --gateway-name myApplicationGateway -n myCertName --cert-file myPfxFile --cert-password myPassword
Example:
az network application-gateway ssl-cert create -g rg-helloworld --gateway-name agw-helloworld -n tpham.net --cert-file tpham-cert.pfx --cert-password myPassword
We need to update our AGW to use the new certificate that we uploaded and tell it to create HTTPS listener and rule that redirect helloworld.tpham.net to our hello-world application.
Update our ingress.yaml with the following example (changes are highlighted in red):
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: hello-world-ingress
annotations:
kubernetes.io/ingress.class: azure/application-gateway
appgw.ingress.kubernetes.io/appgw-ssl-certificate: "tpham.net" #The certificate name
spec:
defaultBackend:
service:
name: hello-world-svc
port:
number: 80
rules:
- host: helloworld.tpham.net
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: hello-world-svc
port:
number: 80
Apply the new changes:
kubectl apply -f .\ingress.yaml
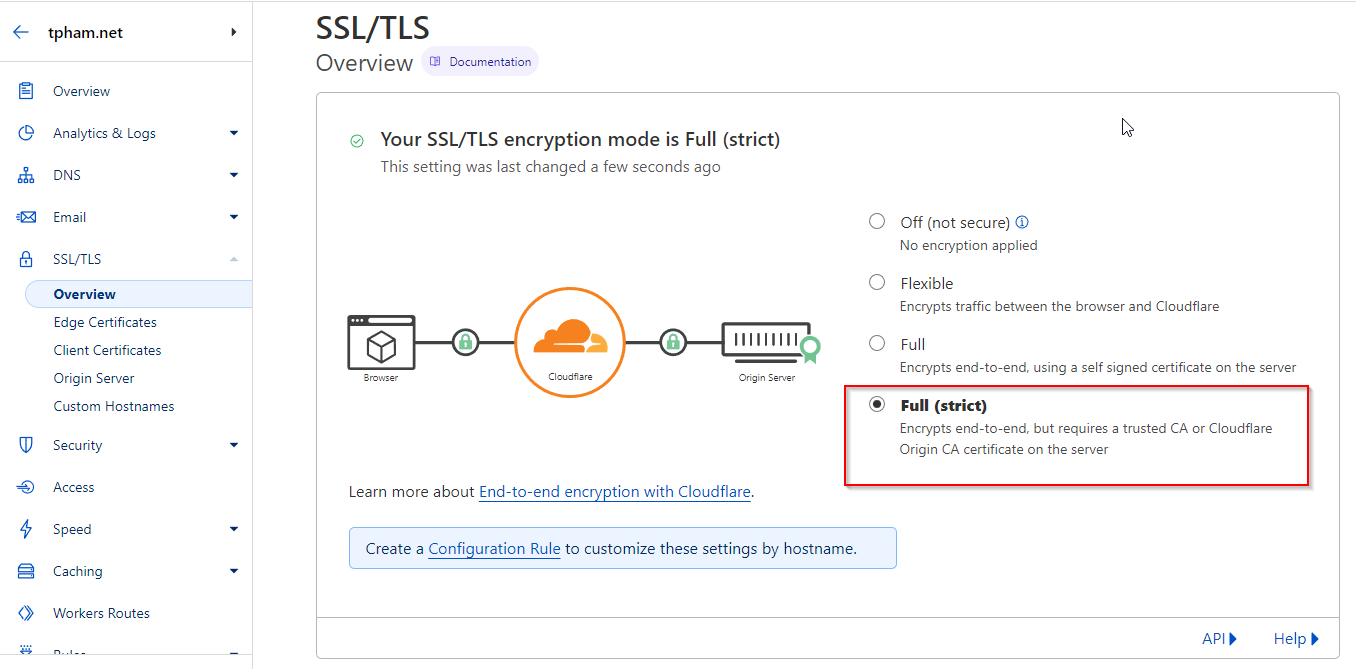
To enforce end-to-end encryption, set the SSL/TLS mode in CloudFlare to Full (strict):
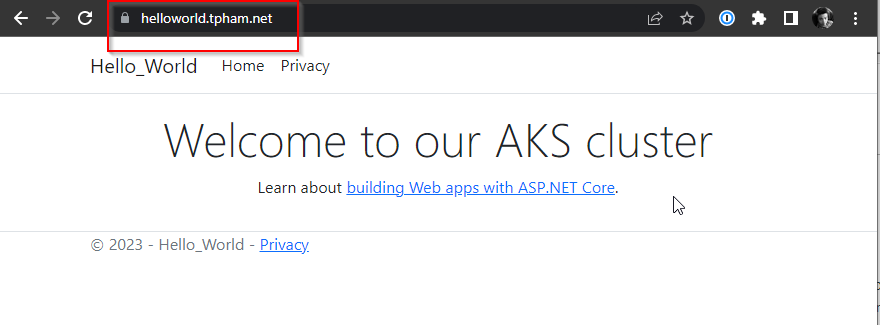
We can now visit our hello-world application from our custom domain.